Is Cyber Security a Good Career?
It’s a great time to have a Cyber Security Career. The BLS found it is one of the fastest growing fields. In fact, it’s projected to grow at a 28% rate. That rate stands on a market that held 100K jobs for 2016. That is for only one prime Cyber Security position – Information Security Analyst. The growth of this field has led to more jobs. At the rate of growth, there will be great demand for the long term. This is a good reason to think of this as a place to start a career and to continue on.
Part of the job growth is due to demand in information technology. The rise of cyber crime has grown that demand. The DHS, found the risk of cyber theft and cyber attacks grows as cultures connect. Cyber criminals use advanced and scalable tools to breach privacy. This is shown by a study by Privacy Rights Clearing House. This study shows that two billion data records were compromised in 2017. Cyber crime also breached more than 4.5 billion records in the first half of 2018. Concerned about viruses? Hackers create four new malware samples every second.
A bachelor’s degree holder could enter the work force as an Info Sec Analyst. This is prime area for Cyber Security careers. The most often cited stats about the large growth in Cyber Security refer to this career path.
Masters and PhD level jobs may include Info Research Scientists and Systems Managers. These are careers with a six figure average salary. They also have lots of clout. Then there is the top level of Cyber Security pros. This job needs a combo of advanced ed and years of experience. Jobs like Certified Information Systems Security Officer (CISSO) are C suite. That means a big salary and a lot of responsibility. These jobs have hardcore requirements. The bottom line of the org lies with these people.
How to Start a Career in Cyber Security
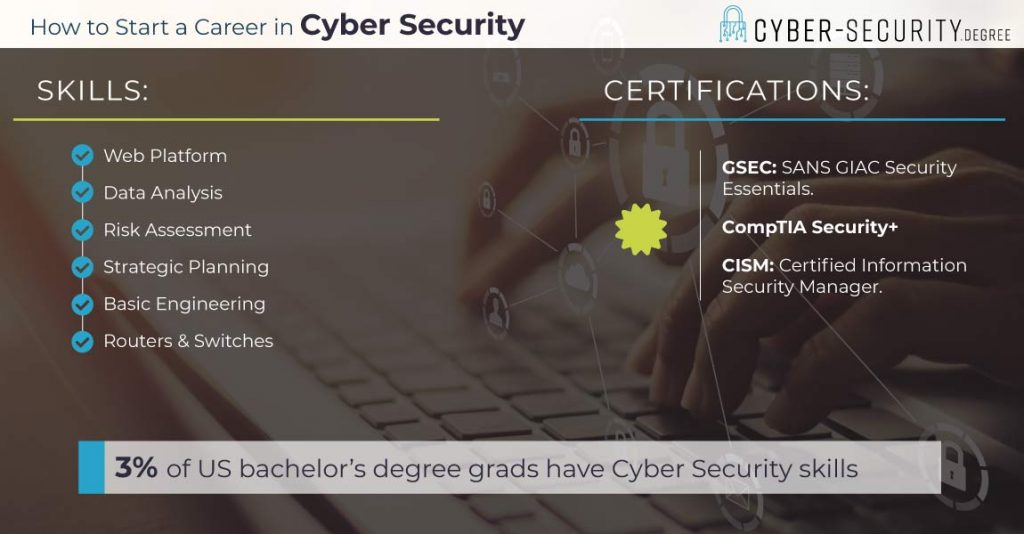
The first step toward a Cyber Security career is to assess. Figure out where you stand and what degree program works best. Perhaps you finished high school and are not sure about college. You may want to consider an Assoc degree or cert program to grow your skill set. If you know you want a bachelor’s program, start with a search for Cyber Sec programs. As a non traditional field, you do not have to take a classic route to become a Cyber Security professional. Some students go straight for certs.
Top 5 Certifications
The IT field holds certs in high esteem. This is true for those in security. Certs show your skills. It’s a shortcut that shows an employer you are qualified. There is no order for getting certified. These five certs are often requested by employers. It may be smart to start with them.
- CEH: Certified Ethical Hacker – Crucial for those set on an Ethical Hacker career. Ethical hacking jobs are a part of the Cyber Security field.
- CISM: Certified Information Security Manager – Mgmt level cert. You need experience in the position to sit for his four hour exam. Great springboard for promotion opportunities.
- CompTIA Security+ – Industry standard for any Cyber Security career. It is two exams. But it is the critical starting point for cert. So, take it when you are ready to job search.
- CISSP: Certified Information Systems Security Professional. – Global and the most popular IT certification for almost 30 years. International Data Corporation (IDC) did a study. Data shows those with CISSP get pay hikes quicker than those without a cert.
- GSEC: GIAC Security Essentials – This back to basics cert covers IT forensics and sec. Consider this a resume boost for the start of a Cyber Security career.
Types of Cyber Security Jobs
Cyber Sec degree holders are lucky. They have many job choices. Their skills are in high demand. It’s a matter of picking a cyber security expert job that you want. Here are some job titles.
Ethical Hacker
A CEH looks for weakness in a computer system. They are a hacker with a conscience. They need to think like a standard hacker. CEH’s also need outlaw knowledge and tools. It is the only way to protect a system from those with bad intent. Lawful and legit actions are essential. This is not any typical tech programmer at work.
An entry level CEH works in a similar way to a Web Developer or Comp Programmer. So, those job salaries may give a range for what a Certified Ethical Hacker might make. There is not hard salary data for this career as of yet. It is also more specialized than those positions. Keep that in mind.
Penetration Tester
These testers and White Hat Hackers work together. They share the same goals. Pen testing is one of the many tools in an Ethical Hackers crucial set.
Pen Testing pokes at vulnerabilities like a hacker. Their methods find which areas of a network have holes. They do this to find methods and windows of entry a hacker could exploit. That way an org knows where and how they need to address weak spots. A Pen Tester also looks for passive threats like sec practice and policy flaws.
IT Auditor
An IT Auditor works like a detective. They find and investigate issues in computer systems. This job starts with CISA cert. That’s because it’s specific to IT auditing. It delves IT security, auditing, cyber threats, and risk mgmt. Notice that none of these domains fixes the problems. IT Auditing is about assessment.
This work identifies challenges and determines their impact. They do not resolve the issue. A keen eye for evaluation is an important part of this career. Auditors report these detailed observations. They can act as a security consultant. This report is the crux of their work. Get ready to keep detailed records in an IT Auditor career.
Computer Forensics Investigator
A Comp Forensics Analyst finds an issue and the origin. In a hack situation, they also recover compromised data. Comp Forensics Investigators help determine the facts in a crisis. They work as part of a legal investigation and with law enforcement.
A Comp Forensics Analyst needs both Cyber Security and criminal justice training. The CFCE cert is a perfect example of this. Validation as a Certified Forensic Computer Examiner (CFCE) meets both demands.
Information Security Analyst
Companies may have an IT dept. It may be led by an Info Security Analyst or chief information security officer. They protect the networks. That means prevention with software, firewalls, and encryption programs. they also react when a breach occurs to an operating system. These analysts write up reports to document challenges.
These cyber security analysts also stay on top of the latest IT tech and trends to keep their company up to date. They set and maintain standards and practices for employees to keep info safe. Many also conduct test cases. That means trying out a “what if” scenario to play out what might happen in the case of a hack or breach. Then they can use that learning to improve their systems even more.
Cyber Security Engineer
A Cyber Security Engineer creates computer security procedures and software systems. They tailor these intrusion detection and prevention tools to their organization. One of their major responsibilities is to handle tech issues for all computer security matters. So, they must have exceptional incident-response skills. Security Engineers also need a high level of computer forensics competence.
They work with other engineers and IT to keep company computer systems efficient.
Network Security Administrators
These pros design and install a network security policy across the network. They have skills in threats and vulnerabilities, as well as protection strategies. Usually they collaborate with engineers to ensure network-wide security.
This position may include identifying network weakness as a security architect. it may also mean designing and managing network protection procedures and policies. Installing and configuring software and tools, as well.
Chief Information Officer
This is a top position in Cyber Security jobs. We’re talking C-suite. That means Chief Info Officer and Chief Tech Officer. That means a great opportunity. it also means responsibility. The bottom line sits in your lap.
Some items on a CISO to do list may include upgrades for company systems. They direct hardware and software needs. Security is in their hands. Not only that, they handle personnel, budgets, vendors, and more. It is the biggest of the big jobs.
Cryptographer
A cryptographer is security specialist who uses codes and ciphers to keep info safe. These pros often work in the cyber security field. So, they protect data and messages that are stored and sent using tech.
Cryptographers use knowledge from different fields. These include math, computer science, and info security. And, these pros may work in different industries. Banking, govt, the military, and communications are just a few areas. Sensitive info needs to be protected from data breaches. So, employers in these areas may hire workers who know cryptography.
There are other types of cyber sec jobs. The cyber security industry growth rate is allowing for more jobs. As the field grows there may be a need for more people to fill positions.