What is a Penetration Tester?
A Penetration Tester is also an Ethical Hacker. Pen testers probe vulnerable points in networks and systems. This helps to do two main things. One is to secure them. And the other is to protect them against malicious attacks.
Unlike illegal hackers, pen testers often work with a company’s IT team. The tools and methods they use find points of entry a hacker could exploit. As such, they help a company identify weak areas. As well as spot and manage risks. They also find passive threats like security practice and policy flaws.
What is Penetration Testing?
Pen testing breaks into a system using specific practices. These practices assess servers, systems and network devices. One area used in pen testing is social engineering. It aims to uncover security holes such as weak user passwords.
Testing also includes ways to report findings. This detailed account helps other info sec pros figure out how to solve security problems. Once IT teams and managers have solutions, pen testing reviews them. As such, there are more tests to see if the ‘fixes’ are effective. This feedback also plays a key role in protecting assets.
What Does a Penetration Tester Do?
Many use the terms Penetration Testers and White Hat Hackers to mean the same thing. In fact, while they share some goals, they are distinct. A Penetration Tester first raises the question, “Can a hacker penetrate our security wall?” If they find that yes, a hacker could break in, they succeed.
An Ethical Hacker keeps going to find a solution. They don’t just find the problem. But also set up a new and better way to prevent it from happening again.
What’s the Difference Between an Ethical Hacker and a Penetration Tester?
Pen testing is a pseudo system breach. It aims to spot vulnerable areas, flaws risks, and unreliable issues. It also breaks into an IT system without causing damage. As such, it mimics what cyber criminals attempt. And sees how they would be able to compromise security in a worst case. Many businesses conduct pen tests on a routine basis. They do so to bolster their defense systems. As well as be proactive before trouble arises.
Ethical hacking is an umbrella term. It includes all hacking and related cyber attack methods. One of these methods is pen testing. As an ethical hacker, you also need wide and deep knowledge. This includes skills in programming. And, a solid grasp of hardware so you can find all kinds of system flaws. In contrast, many pen testers have a focused skill set. They need to know and have skills in an area they test.
What Degrees Do Pen Testers Have?
Many pen testers enter the field with a bachelor’s degree. Common majors are IT, comp sci or cyber security. Employers may look to fill other managerial positions too. These often call for a master’s degree or MBA. And often entail tactical planning skills too.
Southern New Hampshire University
- Take advantage of some of the nation’s most affordable tuition rates, while earning a degree from a private, nonprofit, NEASC accredited university
- Qualified students with 2.5 GPA and up may receive up to $20K in grants & scholarships
- Multiple term start dates throughout the year. 24/7 online classroom access.
- Offering over 200 online degree
Popular Programs
Business Administration, Psychology, Information Technology, Human Services…
Purdue University Global
- Experience world-class education online: Purdue Global offers 180 programs at associate’s, bachelor’s, master’s and doctoral levels
- Courses taught by highly respected faculty members who are experts in their fields
- Competency-based ExcelTrack™ Programs may allow you to earn your degree faster and for less money
Popular Programs
Human Services, Business Administration & Management, Medical Assisting, Early Childhood Education…
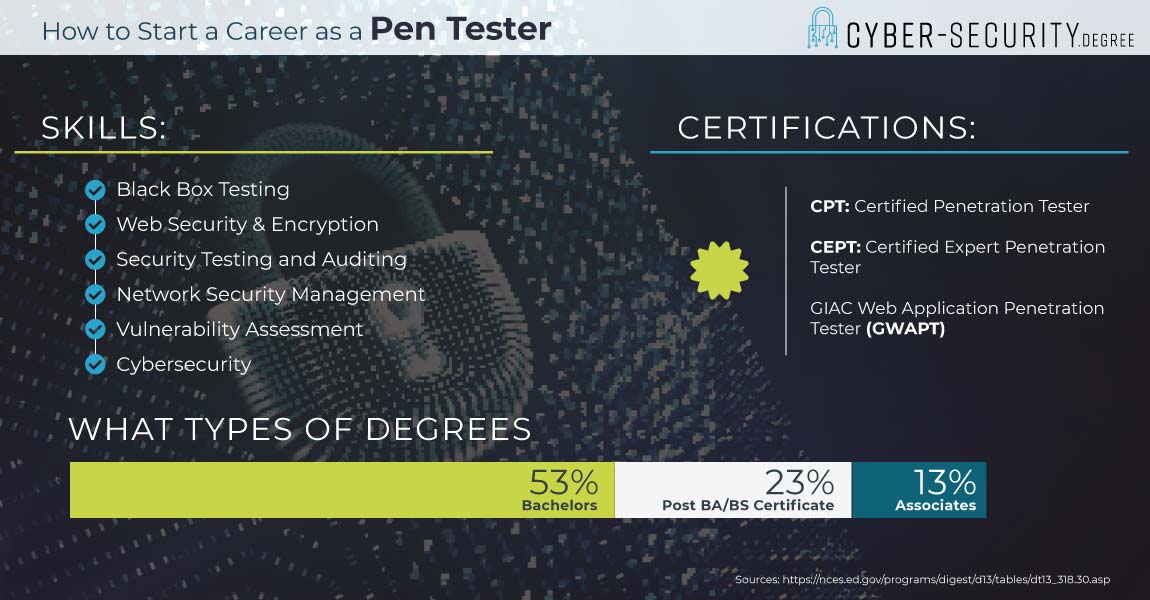
What Skills do you need to be a Pen Tester?
Pen testers need both hard and soft skills. Soft skills are the ones that help a tester solve problems. Or assess a system with a critical eye. Hard skills are the technical ones. Things like conducting a security audit. As well as being able to reverse engineer and develop code.
They also need an ability to automate processes. This means knowing about operating systems. Plus software and network protocols.
Here are five technical skills employers favor.
- Program testing software (E.g. Kalin, Linux)
- Security tools and products (E.g. Fortify, AppScan)
- Digital forensic tools
- Network servers and tools (E.g. Nessus, Burp)
- Metasploit framework
How Much Money Does A Penetration Tester Make?
Pen testers may earn salaries that compare to those of info sec analysts. Info sec analysts earn about $98,350 per year. As this is an average, some earn less and others, more than the norm. At last check, the lowest 10% earned $56,750. And the highest 10 percent earned more than $156,580.
Top Paying States
Cities across the nation offer diverse salary levels for Pen Testers. There are five states that have the most info sec pros. These are Virginia, DC, Maryland, Colorado and Delaware. They report salaries that range from $102,780 to $111,780.
Virginia not only has a high volume of workers. It is also one of the states with the highest salaries too. In fact, workers report average salaries of $111,780 per year. There are four other states which report high salaries. These are Texas, California, New York and Florida. All five are the top paying states.
But from this list, New York is the top paying. Info sec analysts in NY report an annual average salary of $122,000.
| City | Median Salary |
| Atlanta | $98,500 |
| Chicago | $95,246 |
| Charlotte | $93,618 |
| Washington | $90,360 |
| Phoenix | $81,407+6 |
Pen Testing Job Titles to Look For
Information security is a broad field. As such, pen testers may find postings with a range of job titles. Here are a few examples.
- Senior Penetration Tester
- Information Security Engineer
- Continuous Penetration Tester
- Security Analyst with Active CPT Certification
- Automation Penetration Tester
Pen Testing Certifications
A wide range of certifications exist for pen testers. These prove you have a specific set of skills. And may help a resume stand out when you apply for a job. Here are some common ones you might think about.
Certified Penetration Tester CPT
The CPT certification is basic. As a result, it shows you have essential skills of pen testers.
- Pen testing tools
- Network protocol attacks
- Network recon
- How to spot weak areas
- Windows exploits
- Unix/Linux exploits
- Covert channels & rootkits
- Wireless security Flaws
- Vulnerable areas in web apps
GIAC Certified Penetration Tester GPEN
The GIAC Offers over 20 specialized info sec certifications. As such, it does not take a one-size fits all approach. Instead, it tests real world skills in technical subjects.
Certified Expert Penetration Tester CEPT
The CEPT certifies that you have expert level skills in pen testing. This includes mastery of these areas.
- Pen testing methods
- Network attacks
- Network recon
- Windows shell code
- Linux & Unix shell code
- Reverse engineering
- Memory Corruption /Buffer Overflow
- Exploit Creation