Getting into Cyber Security with a General IT Background
Pursuing a cyber security role with a general IT background may be a great move. In fact, many employers look for cyber security pros who have other kinds of IT work experience. Some entry level job titles may be penetration tester, incident analyst, or IT auditor.
So how could you transition from IT pro to cyber security expert?
For one, you could update your education. Security pros like Information Security Analysts need to earn at least a Bachelor’s degree. But, many go a step further and earn a Master’s degree – like an MBA in Information Systems.
You could also earn an information security certification. Earning one could be a chance to learn new cyber security skills. You could earn a more general certificate, like Certified Information Systems Security Professional (CISSP). Or, you could certify in a certain skill area, like ethical hacking.
And, you could look for cyber security roles that may build on your past experience. For instance, a computer systems analyst may be able to pursue a systems security role. A database admin could pursue a database security role.
Cyber Security Jobs to Target
These entry level cyber security positions might be a step toward a cyber security career path:
Computer Programmer
Programmers write code for software and computer applications. They also test the code to make sure it’s bug free. Programmers could pursue enhanced roles, after they gain experience. These may include cyber security roles – like IT Security Manager.
Network Engineer
These pros plan, implement and oversee the computer networks that support in house voice, data, video and wireless network services.
Computer Systems Analyst
Analysts look at how computer systems work in a company. They find ways to use IT to improve how the company runs. So, many may go on to pursue leadership roles. That could include becoming an IT Security Manager.
Database Administrator
These pros store and organize data. That could include financial info, shipping records, and more. Security is important when working with data. Some database admins may pursue Information Security Analyst roles that involve database security. Others may pursue IT Security Manager roles.
Penetration Tester
Pen testers probe vulnerable points in networks and systems. Penetration testing helps to do two main things. One is to secure them. And the other is to protect them against malicious attacks.
Computer Support Specialist
Support specialists give customer service to computer users. They could work in all different areas. For instance, they could support a business or help home computer users. Many end up pursuing other IT career paths. These could potentially involve cyber security.
Software Engineer
Engineers design software programs. They also manage the process of building the software. That includes planning for security concerns. Software engineers could pursue IT manager roles. These roles may call for knowledge of cyber security.
IT Auditor
IT Auditors bridge the gap between finance and computer science. They collect systems data and information to analyze tech performance. This means that they score the effectiveness of a company’s tech systems.
Purdue Global
- Experience world class education online!
- Purdue Global offers 180 programs at associate’s, bachelor’s, master’s and doctoral levels
- Competency-based ExcelTrack™ Programs may allow you to earn your degree faster and for less money
- Cyber Security Programs Include:
BS in Cyber Security
MS in Cyber Security Management
Graduate Certificate in Information Security
Southern New Hampshire University
- Take advantage of some of the nation’s most affordable tuition rates, while earning a degree from a private, nonprofit, NEASC accredited university
- Multiple term start dates throughout the year. 24/7 online classroom access.
- Cyber Programs Include:
BS in Cybersecurity – General Track, Data Analytics or Project Management Track
MS Cybersecurity – General Track or IT Management
What Degree Do You Need to Get into Cyber Security?
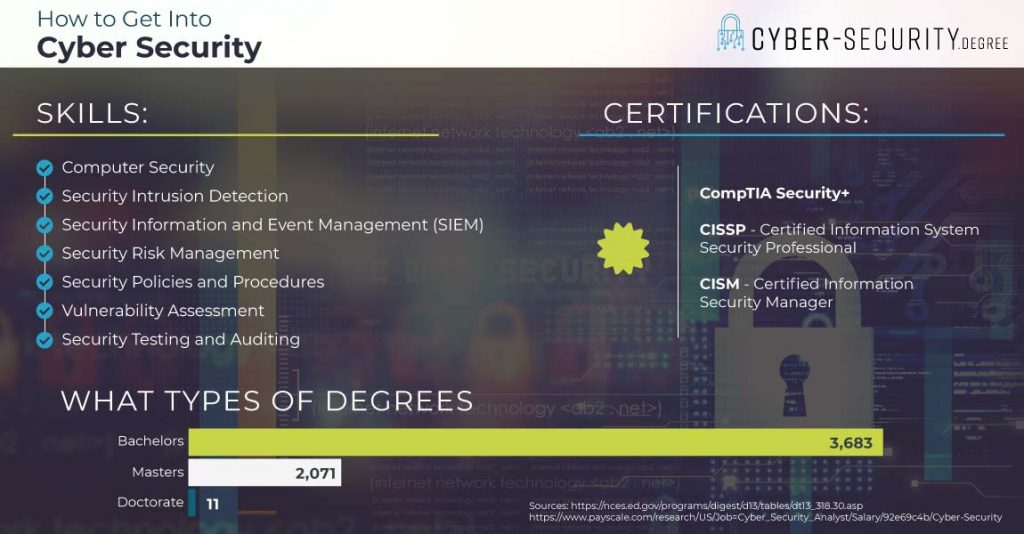
The minimum education for most cyber security career paths is a Bachelor’s degree. For Information Security Analysts, this is usually in an area like computer science, information assurance, or programming. Computer and Information Systems Managers often earn a Bachelor’s in computer or information science. Management information systems (MIS) programs are also common. These include both business and computer classes.
You could even earn a Bachelor’s in Cyber Security. This typically covers security across various areas of the IT field. According to SNHU, you could study how to keep networks secure, respond to a threat, and manage risk.
Many IT security pros also go on to earn a Master’s degree. A Master of Business Administration (MBA) may be common for both Security Analysts and Security Managers. In this program, you could learn how a business runs – including its IT. Information Security Analysts often concentrate in a tech related area. Like, Information Systems.
Or, look into Master’s in Cyber Security programs like the one at Wilmu University. These may offer a broad overview of the field. Plus, you could take in depth courses in skill areas like cryptography. Some are designed so that if your Bachelor’s isn’t tech related, you may still be able to enter the program. (By taking one or more prerequisites, that is!)
What Skills Do You Need to Get into Cyber Security?
Cyber security professionals need to understand how to detect and respond to cyber threats. They need to know how plan for attacks and keep sensitive information safe from hackers. So, they may need skills like:
- Security Intrusion Detection. Often, cyber security pros use an Intrusion Detection System (IDS). This is software that monitors networks for threats like malware. Cyber security experts need to know how to use an IDS and how to respond. You could learn this in a college degree program, in a certificate program, or on the job.
- Security Risk Management. This is all about planning for risk and knowing what to do in the event of a threat. This skill combines management knowledge with an understanding of cyber threats. You may study this in college or in a certificate program. And, you could enhance the skill on the job.
- Security Policies and Procedures. Companies have policies for how to use IT safely. Cyber security experts may help create these policies. That means knowing about best practices for keeping a company’s IT resources secure. You could study the basics in a post secondary IT program. And, you could learn more on the job.
Cyber security pros may also need “soft” skills. These are different from technical skills. They relate to how you reason, communicate, and work with others. Therefore, some useful soft skills for a cyber security career path, according to O’Net may include:
- Critical thinking
- Active listening
- Complex problem solving
- Speaking
- Reading comprehension
How to Gain Practical Cyber Security Experience
You may be able to build cyber security skills on your own. Here are a few ideas for how to pursue experience:
- Learn on the job. If you have a general IT job, could you ask to shadow an IT security pro at your company to learn more? You may already do a lot to keep IT resources safe. Like, using a VPN and changing important passwords regularly. It could be helpful to learn how your role connects to the bigger picture.
- Get hands on, at home. You could create your own computer lab to learn key cyber security concepts. Use old PCs and build a secure network. Then, try to hack it. See if you can strengthen your security and make your network harder to hack.
- Gamify it. Try your hand at cyber security games. Yes, really! There are plenty of games out there to help you practice cyber security skills. War games and Capture the Flag are a couple types. These games may be fun, but they call on real world methods to stop cyber attacks.
- Pursue an internship. This may be a great way to learn how cyber security concepts work in the real world. If you’re in college or recently graduated, find out if your school can help with your search.
- Take a class. If you’re hoping to build a particular skill, see if you can find a course online. Classes in coding, cryptography, and network security are out there. You could even pursue a certification or a degree in cyber security.
Cyber Security Certifications
Certified Ethical Hacker (CEH)
Did you know some hackers exploit threats for good, not criminal reasons? This certificate covers the skills to do just that. You could learn how to use hacking to find vulnerabilities – so you can fix them, of course. Therefore, CEH could be great for network security pros or anyone interested in this field.
CompTIA Security+
This cert bills itself as the first security credential IT pros should earn. It includes basic knowledge used in IT security roles. You could learn about risk management, intrusion detection, cryptography, and more. This cert may be great if you hope to launch or enhance a cyber security career path.
Certified Information System Security Professional (CISSP)
Earning this cert could prove your skills in a few areas. These include designing, implementing and managing cyber security programs. It is not aimed at entry level cyber security pros, though. Therefore, you may want to consider this cert if you already have some expertise in the field. At that point, it might help you enhance your career.
Certified Information Security Manager (CISM)
This cert is all about managing information security programs. It covers incident and risk management, security governance, and a lot more. Earning the cert also comes with resources to help you build your career. It is aimed at those with experience in IS/IT security and control, who hope to pursue a manager role.
Certified Information Systems Auditor (CISA)
CISA is designed for those who audit, monitor, control, and assess IT and business systems. It is aimed at entry level or mid career IT workers. So if you’re just starting out in IT, this cert may be one way to prove your skills and pursue a new direction.
NIST Cybersecurity Framework (NCSF)
This cert covers the Framework, which is an approach to managing cyber security risk. In the course, you’ll learn how to use the Framework to find, assess, and handle cyber security risk. While it covers cyber security basics, it is aimed at those who already have some expertise.
Certified Cloud Security Professional (CCSP)
This cert may prove your skill set in securing IT assets in the cloud. It covers data, applications and infrastructure in the cloud. That includes how to design, manage, and secure these assets. CCSP is aimed at IT and infosec leaders. It’s not an entry level position but may help you enhance your career.
Computer Hacking Forensic Investigator (CHFI)
Learn how to collect evidence on hacking attacks. This cert covers investigation skills needed to find and prosecute hackers. To take the cert, you must have two years of work experience in Information Security. So, this could be a way to build on an entry level cyber security career.
Cisco Certified Network Associate (CCNA)
Learn the skills to work with Cisco networks. This cert covers more than just security. But, learning how to keep Cisco networks secure is a big part of it. This is an entry level cert. But, it may be good to have at least year of experience using Cisco solutions. And, knowledge of network basics and IP addressing also helps.