What is a Network Security Degree?
A Network Security degree studies how to protect information. So, you often learn about safety protocols. These keep networks secure. And prevent data loss at the same time. As this is the focus, you might also gain comp sci skills. One might be learning to install software. Another, to make system upgrades. These help boost a computer network’s chances of staying secure.
While you learn learn these things, it may help you gain key skills. For instance, you are likely to problem solve. And may also learn to analyze. One thing you may analyze is risk. And this means knowing how to check issues with data communication. Then, to also pin point weak areas in the data protection.
What are The Different Types of Network Security?
There are three parts of network security. Each of these parts needs specific tools. And, entails an understanding of how to use them.
- Hardware
- Software
- Cloud services
So, in a broad sense, network security refers to many counter measures.
These are in place for two reasons. The first is to protect the network. Second, to also protect any data stored on it. Or passing through it.As a result, network security aims to keep data safe from cyber attacks. But people use it to prevent many things. Like hacking, phishing and unauthorized access. Here are a few types of network security to know about. Often, you learn to leverage these tools. Then also, to set up and keep an effective line of defense.
Network Access control (NAC)
NAC creates compliance standards and practices. And is in place so that only authorized network users have access. It also ensures there are security policies. Also, that these enforce limits to access. So, it often uses tools like anti virus and anti malware software.
Application security
Software applications can have holes. As such, attackers can use them to infiltrate your network. So, it is vital to check apps for security. And install firewalls to protect them from compromise.
Behavioral analytics
To spot abnormal network behavior, you need to know “normal” behavior. Luckily, there are behavioral analytics tools for this. These tools find activity that veers from the norm. And, help companies detect security issues. Then also help them to remediate the threats.
Data Loss Prevention (DLP)
The largest culprit when it comes to data loss is through staff. As such, a business must act. DLP tools are part of this process. They set up staff protocols. And prevent them from sending private data outside the network. Some of the other things DLP tools do is manage process. For instance, any time staff uploads content. Or tries to forward it.
Email security
A number one threat for security breach are email gateways. This is because attackers use social engineering tactics. One is to deceive recipients. And then send them to malicious sites. Thanks to hacked data and sold email lists, security is key. So, there are many email security tools to use. These can block attacks. Also, they can also control and edit outbound messages. And thus prevent loss of email data.
Firewalls
Firewalls are an internal network fortress. As such, they presume that all info outside the networks isn’t trustworthy. In creating a firewall one can do a few things too. One is to set defined rules. And, so allow or block traffic.
Computer Forensics
Hacks and breaches happen. So, a business may need to do a few things. First, they need to prepare for the worst. Second, they also need to prep how to handle when it happens. That’s what forensics covers. It investigates after a hack or breach. And looks for ways to contain it or remediate it.
Network Segmentation
Segmentation classifies network traffic. So, it makes it easier to enforce security policies. For example, it sets up categories and IP addresses. As such, it bases access rights on role and location. And thus may help a network spot suspicious activity.
Security Information and Event Management
After a crisis there are tools to help restore order. Some are of them are forensic security products. For instance, SIEM products. These gather information. So, may help to identify and respond to threats.
Why is Network Security Important?
When anyone or any event compromises data, it has grave risks. All you have to do is think of someone hacking your bank account. Then, multiply this loss and disruption with one more step. For one, imagine what would happen if a cyber criminal accessed all the bank’s data?
This exercise may help you grasp the need and import of network security. But there’s more. Cyber threats are also rising fast. In fact, experts say that malicious hackers attack every 39 seconds. Now, network security aims to combat this. And uses system checks and network protocols to do so. As such, more companies want to focus on it.
Southern New Hampshire University
- Take advantage of some of the nation’s most affordable tuition rates, while earning a degree from a private, nonprofit, NEASC accredited university
- Qualified students with 2.5 GPA and up may receive up to $20K in grants & scholarships
- Multiple term start dates throughout the year. 24/7 online classroom access.
- Offering over 200 online degree
Popular Programs
Business Administration, Psychology, Information Technology, Human Services…
Purdue University Global
- Experience world-class education online: Purdue Global offers 180 programs at associate’s, bachelor’s, master’s and doctoral levels
- Courses taught by highly respected faculty members who are experts in their fields
- Competency-based ExcelTrack™ Programs may allow you to earn your degree faster and for less money
Popular Programs
Human Services, Business Administration & Management, Medical Assisting, Early Childhood Education…
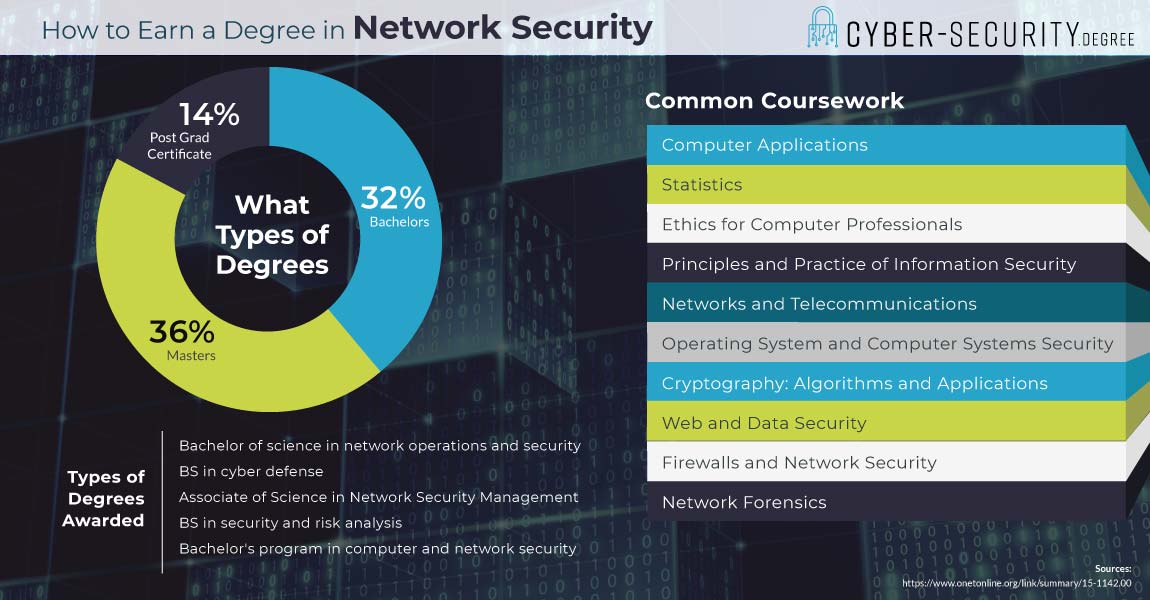
Types of Network Security Degrees
There are Network Security degree programs at all levels. From associate and bachelor’s. To master’s, and doctorate degrees.
Undergrad Degrees
Associate degrees are usually two year programs. They may help you enter the work force. Or, provide transfer credits for a bachelor’s. Bachelor degrees are college degrees. And, usually take four years to complete. They also aim to provide skills for entry level jobs.
Grad Degrees
Masters degrees are often for people who want to advance. They usually take two years. And, may help you learn to lead and manage projects. PhDs are research degrees. And, the highest level of info sec degree. As such, they are often for people who want to innovate.
Network Security Degree Course Curriculum
No two network security degree programs are the same. But they usually cover three key concepts. And are sometimes called the “CIA triad.” These elements are as follows.
- Confidentiality
- Integrity
- Availability
A network is secure only when it has all three elements in play. They also need to be in play at the same time. As such, you may study each in depth. And, how they interact.
Core Curriculum:
- Basics of Information SecurityIn this type of class, you may learn about basics. For instance, all the tools, concepts and methods of security. You may also learn how to set up a security system. And, to check it for viruses and trojans.
- Operating SystemsThe main focus of this type of class is operation systems. So, you may learn the finer points of backing up data. And also, how to protect web and data systems.
- Network ForensicsThis type of class looks at the ways to investigate a cyber crime. So, you may learn how to do a security audit. And, to search, collect, analyze and report findings of breaches.
How Long Does It Take to Earn a Degree in Network Security?
It may take four years for a full time student to earn a bachelor’s degree in network security. But, if you have transfer credits, it may be faster. For instance, some people earned an associate degree. So, they may only have two years of study left.
Top Schools for Network Security Degree Programs
NCES lists 14 institutions with Information Technology Security Programs Bachelor’s level and above. From those schools, 2,661 degrees were awarded to students in 2016.
| School | 2016 Degrees awarded | 2018/19 Graduate Tuition |
| University of Maryland-University College | 1226 | $11,976 |
| Western Governors University | 652 | $5,780 |
| University of Phoenix-Arizona | 531 | $11,219 |
| American Public University System | 310 | $6,480 |
| ECPI University | 281 | $14,720 |
| Capella University | 211 | $8,726 |
| Baker College | 154 | $9,000 |
| Clover Park Technical College | 148 | $10,736 |
| Ferris State University | 136 | $17,910 |
| St Petersburg College | 129 | $ 9,717 |
Information Systems Security Careers
| Career | Entry level education | Average Median Salary | Projected growth rate |
| Network Security Management | Master’s | $142,530 | 12% |
| Security Engineer | Bachelor’s | $84,935 | 6% |
| Security Architect | Bachelor’s | $109,020 | 6% |
| Security Specialist | Bachelor’s | $82,050 | 6% |
Network Security Certifications
There are many network certifications to look for. After your degree, they may bring value to a resume. And, often help you gain expert and technical skill sets.
Information Systems Security Engineering Professional
The U.S. National Security Agency (NSA) helped create ISSEP. Or, the Information Systems Security Engineering Professional. ISSEP certifies the holder knows the basics of security engineering. And is a useful tool specific to engineers. To earn an ISSEP, you take a three-hour exam. It has 150 questions and 700 out of 1,000 is a pass.
Certified Reverse Engineering Analyst
CREA is Certified Reverse Engineering Analyst. For info sec this is all about analyzing malware. So, encryption plays a key role. In fact, the CREA mission is to break down malware. And to do it with analysis and decryption.